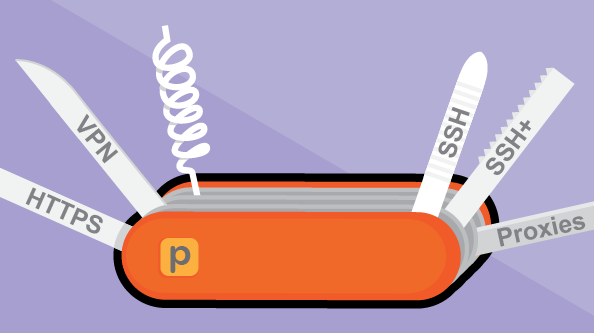
What Is Psiphon?
Psiphon was created by the Internet-freedom center “Citizen Lab” at the University of Toronto, before being handed off to a private group for management and upkeep, including – full disclosure – VOA’s parent agency, the Broadcasting Board of Governors.
Released in 2004, Psiphon offers VPN-like security and encryption in a fast, easy-to-use design. Unlike tools such as Tor or PGP, Psiphon employs a variety of technical tricks (HTTPS, SSH+, proxy servers and others) rather than one specific design to help users evade online censorship.
The first versions of Psiphon were built around something called the “trust model,” meaning users first had to be invited to join in by someone already using Psiphon, such as a friend, family member or a trusted contact living in a country with no censorship of the web. The latest versions of Psiphon, however, have dropped this requirement.
Another key difference between Psiphon and many other circumvention tools is there’s no bulky software to download and install. All services can be accessed online, meaning that for those users concerned about having their computers searched for banned software, there’s nothing to find.
How Psiphon works
Each successive version of Psiphon has become easier to use, and the latest version – Psiphon3 – has the lightest footprint.
It works like this: a user downloads a small executable file, either directly onto their computer or to a memory stick that can be passed around user to user. When the file is opened, a Windows security notice will appear asking whether or not to run Psiphon. This is an important verification step: because Psiphon is just a small executable file and not a full program, the Windows security notice automatically generates a security certificate – something like a digital thumbprint that confirms the file is authentic and not malware.
Once a user clicks “run,” the file automatically opens the client window, which is a small Windows box with the Psiphon logo, a few options boxes, and a blue spinning arrow. Each client window comes with a constantly updated list of servers it can connect to, whether via SSH+, SSH or VPN.
Psiphon will then try to connect with one of the verified servers to connect to the encrypted Psiphon network. While connecting, the blue arrow will continue to spin, and once it finds and connects to a server, the arrow turns into a green checkmark. Once users see that checkmark, they know that all their Internet traffic is now tunneling through the Psiphon network, which will allow them access to blocked or censored sites.
How can Psiphon help me?
Psiphon is a fairly robust circumvention tool and provides some, but not complete, privacy protection. Because users access it online, it can be very useful when accessing banned websites from public computers, for example those at a cyber café. Assuming those computers don’t have keystroke-logging spyware, and the browsing history is deleted after use, it can be hard to trace.
Let’s say you want to visit Facebook, but that site is blocked in your country. Once you have a Psiphon account, you can log in through a network of proxy servers which connect to the main Psiphon server. Once there, the secure Psiphon blue browser window will appear underneath your browser’s standard address window. It’s not guaranteed – nothing is – but it can make accessing banned websites much easier.
Possible drawbacks
There are two major drawbacks. First, Psiphon is only designed to work on Windows and Android systems, putting it out of reach for Apple or other OS systems.
Second, Psiphon is not designed as a complete anonymizing tool like Tor.
While traffic routed within the Psiphon network is encrypted, there’s nothing stopping anyone from detecting that your computer is connected to a known Psiphon server. Additionally, those Psiphon servers, while constantly changing, do not protect against outside traffic analysis, meaning that with sophisticated tools, a government could probe to detect the users identity and any unencrypted traffic flowing through the server.
Some analysts have also speculated that Psiphon’s particular design could make it vulnerable to man-in-the-middle attacks. In such attacks, a hidden user can access the secure information flowing between two points on the Internet, making it look like a secure connection but in actuality intercepting the data flows.
The bottom line
Psiphon has proven to be a fairly robust tool to evade government censorship and, to a lesser degree, protect your privacy. It’s easy to use, and because it runs as a client – sort of like a cloud-based application – there’s little danger that authorities will find evidence of your using Psiphon online.